A series of critical vulnerabilities in the smart devices developed by Nexx could let hackers open people’s garage doors, disable their home alarms, and turn off smart plugs.
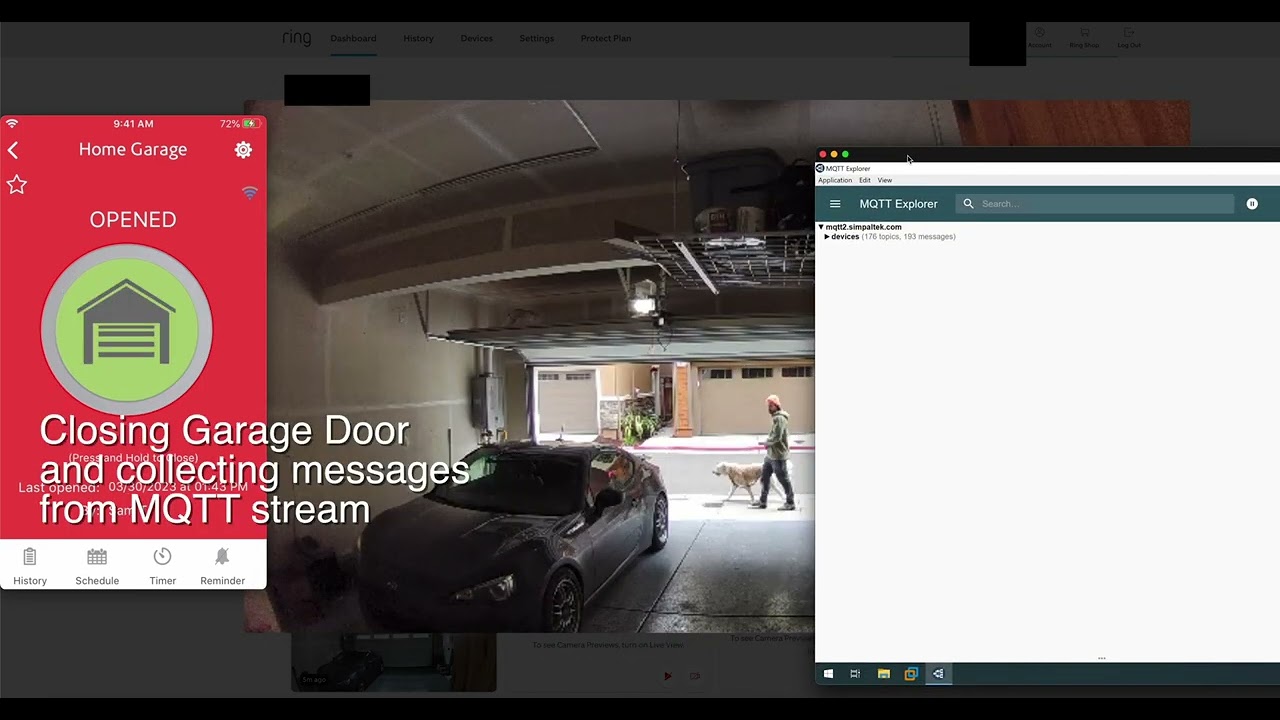
The security holes were discovered by independent researcher Sam Sabetan, who demonstrated the findings in concerning proof-of-concept video. Sabetan managed to control his garage door, explaining that any malicious actor would be able to do it remotely.
Smart homes are rapidly gaining traction, and the main benefit is convenient access from a mobile device. With mobile phone integration and support for Android and CarPlay, smart home devices, including garage doors, can be controlled with voice commands or right from the display in the dashboard.
Automations based on location could make the integration even more convenient, as garage doors could open automatically when you arrive home.
Sabetan says the process comes down to several steps required for each user when connecting new devices to their Nexx accounts. In the mobile app, the user must initiate a first connection to Nexx Cloud. When this happens, the cloud service generates a password and sends it to the device specifically for communication purposes.
This password is submitted to the mobile device first and is then transmitted to the smart device, such as the garage door controller, via Bluetooth or Wi-Fi. Thanks to this password, the smart device can connect to the cloud, establishing the connection that eventually lets users control it from the smartphone.
The problem resides in how Nexx generates the passwords. The researcher discovered that Nexx generates a universal password for all devices. This password is hardcoded in the firmware of the device but is also shared in the API offered to software developers.
What’s even more concerning is that a malicious actor would be able to identify customers using the information included in messages broadcasted by the cloud service. Sabetan says Nexx exposes information like emails, device IDs, and first names with last initials in the broadcasted messages whenever a customer sends a request to open a garage door.
Sure enough, exposing personal details is already a major security concern, but because it all happens when the customer sends a command to open the garage door, a potential hacker can do the same thing as well. In other words, the bad actor can replay the message and eventually open the garage door as well using the credentials exposed by the Nexx server.
The security researcher discovered that a similar flaw also exists in smart alarms, eventually uncovering other vulnerabilities in smart plugs too.
But in most cases, these companies work together with security researchers specifically to identify the bugs, determine the cause, and then release a fix.
In the case of Nixx, this didn’t happen. Sabetan says he first reached out to the firm in early January when he opened tickets on the official support website. After his tickets were closed, he tried to contact the Nexx founder directly using the personal Gmail address found in FCC filings. No response was received.
Eventually, the researcher decided to ask the Cybersecurity & Infrastructure Security Agency, also known as CISA, for help. As an agency of the United States Department of Homeland Security, CISA plays a key role in helping companies patch vulnerabilities in a timely manner.
Not in this case though, as CISA’s federal team failed to get in touch with Nexx. Their attempts were unsuccessful, and so were Sabetan’s repeated warnings that the findings would eventually be published online.
Vulnerabilities found in the software and hardware are eventually disclosed online as a way to force parent companies to develop urgent fixes. It’s not yet known if Nexx is at least working on a patch, but for now, thousands of customers are affected.
The researcher says he estimates that approximately 40,000 devices are exposed by the unpatched security vulnerabilities. They are used in both residential and commercial properties, so eventually, a hacker would be able to open the garage door to someone’s house. There are over 20,000 active Nexx accounts, Sabetan warns, and they could all be vulnerable to remote attacks until a patch is released.
The solution to block any potential exploits is painful, to say the least. The researcher says there’s no other way to secure your smart home than unplugging all Nexx devices as soon as possible. Of course, reaching out to the parent company and insisting on emergency fixes is something all customers do, hoping that Nexx would eventually acknowledge the issues and pay more attention to securing their products.
Smart homes are rapidly gaining traction, and the main benefit is convenient access from a mobile device. With mobile phone integration and support for Android and CarPlay, smart home devices, including garage doors, can be controlled with voice commands or right from the display in the dashboard.
Automations based on location could make the integration even more convenient, as garage doors could open automatically when you arrive home.
Universal passwords
The way Nexx has secured the connection to its servers, however, is exposing critical data.Sabetan says the process comes down to several steps required for each user when connecting new devices to their Nexx accounts. In the mobile app, the user must initiate a first connection to Nexx Cloud. When this happens, the cloud service generates a password and sends it to the device specifically for communication purposes.
This password is submitted to the mobile device first and is then transmitted to the smart device, such as the garage door controller, via Bluetooth or Wi-Fi. Thanks to this password, the smart device can connect to the cloud, establishing the connection that eventually lets users control it from the smartphone.
The problem resides in how Nexx generates the passwords. The researcher discovered that Nexx generates a universal password for all devices. This password is hardcoded in the firmware of the device but is also shared in the API offered to software developers.
What’s even more concerning is that a malicious actor would be able to identify customers using the information included in messages broadcasted by the cloud service. Sabetan says Nexx exposes information like emails, device IDs, and first names with last initials in the broadcasted messages whenever a customer sends a request to open a garage door.
Sure enough, exposing personal details is already a major security concern, but because it all happens when the customer sends a command to open the garage door, a potential hacker can do the same thing as well. In other words, the bad actor can replay the message and eventually open the garage door as well using the credentials exposed by the Nexx server.
The security researcher discovered that a similar flaw also exists in smart alarms, eventually uncovering other vulnerabilities in smart plugs too.
The more concerning part
Security vulnerabilities are nothing new, as such problems are regularly found even in products from companies with more solid know-how in the software industry. Microsoft issues security patches for Windows and Office every month as part of a cycle called Patch Tuesday.But in most cases, these companies work together with security researchers specifically to identify the bugs, determine the cause, and then release a fix.
In the case of Nixx, this didn’t happen. Sabetan says he first reached out to the firm in early January when he opened tickets on the official support website. After his tickets were closed, he tried to contact the Nexx founder directly using the personal Gmail address found in FCC filings. No response was received.
Eventually, the researcher decided to ask the Cybersecurity & Infrastructure Security Agency, also known as CISA, for help. As an agency of the United States Department of Homeland Security, CISA plays a key role in helping companies patch vulnerabilities in a timely manner.
Not in this case though, as CISA’s federal team failed to get in touch with Nexx. Their attempts were unsuccessful, and so were Sabetan’s repeated warnings that the findings would eventually be published online.
Vulnerabilities found in the software and hardware are eventually disclosed online as a way to force parent companies to develop urgent fixes. It’s not yet known if Nexx is at least working on a patch, but for now, thousands of customers are affected.
The solution to block any potential exploits is painful, to say the least. The researcher says there’s no other way to secure your smart home than unplugging all Nexx devices as soon as possible. Of course, reaching out to the parent company and insisting on emergency fixes is something all customers do, hoping that Nexx would eventually acknowledge the issues and pay more attention to securing their products.